 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Confidential computing is a technology that aims to enhance data privacy and security by providing encrypted computation on sensitive data and isolating data from apps and other host resources in a fenced off enclave during processing. The concept of confidential computing is gaining popularity, especially in the cloud computing space where sensitive data is often stored and processed.
However, there are some who view confidential computing as an unnecessary technology and a marketing ploy by cloud providers, aimed at calming customers who are cloud-phobic.
In this Breaking Analysis, we revisit the notion of confidential computing and explore whether it’s just marketing or a key part of a trusted security strategy. To do so we’ll invite two Google LLC experts to the show. But before we get there, let’s summarize the overall market climate briefly with some Enterprise Technology Research data.
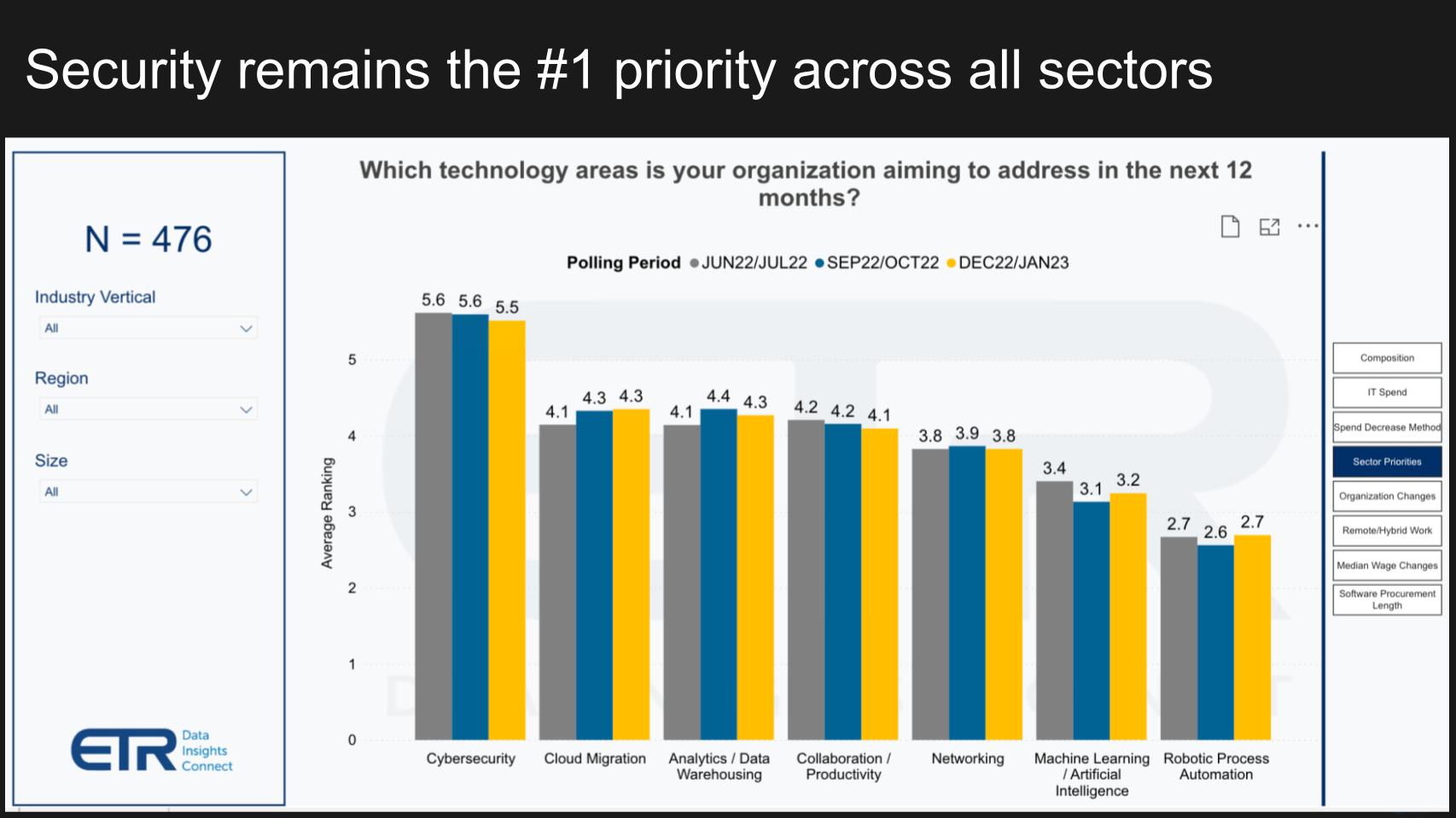
There’s not a ton in the ETR dataset on the topic of confidential computing. It’s a technology that’s deeply embedded into silicon and computing architectures, so it’s not as visible to chief information officers and the information technology decision makers in ETR’s quarterly surveys. But at the highest level, security remains the No. 1 priority being addressed by organizations in the coming year, as shown above.
This is pretty much across the board by industry, by region and by size of company. The only slight deviation from the mean is in financial services. The second- and third-most-cited priorities, cloud migration and analytics, are noticeably closer to cybersecurity than other sectors, likely because financial services has always been hyper security-conscious. But security is still a clear No. 1 priority in that sector.
The idea behind confidential computing is to better address threat models for data in execution. Protecting data at rest and data in transit have long been a focus on security technologies, but more recently, silicon manufacturers have introduced architectures to separate data and applications from the host system. Arm Ltd., Intel Corp., Advanced Micro Devices Inc., Nvidia Corp. and other suppliers are all on board as are the big cloud players and system manufacturers such as Dell Technologies Inc., IBM Corp. and Hewlett Packard Enterprise Co.
The argument against confidential computing is that it narrowly focuses on memory encryption and it doesn’t solve the biggest problems. Multiple system images, updates, different services and the entire code flow aren’t directly addressed by memory encryption. Rather,11 to truly attack these problems, many believe that operating systems need to be reengineered with the attacker in mind. There are so many variables and at the end of the day, critics say the emphasis on confidential computing made by cloud providers is overstated and largely hype.
This tweet above from security researcher @bsdaemon sums up the sentiment of many skeptics. He says:
Confidential computing is mostly a marketing campaign for memory encryption. It’s not driving the industry towards the hard, open problems… it is selling an illusion.
Nonetheless, encrypting data in use and fencing off key components of the system isn’t a bad thing… especially if it comes with the package essentially for free.
There has been a lack of standardization and interoperability between different confidential computing approaches and the Confidential Computing Consortium was established in 2019, ostensibly to accelerate the market and influence standards.
Notably, Amazon Web Services Inc. is not part of the consortium possibly because: 1) The politics of the consortium were a conundrum for AWS as the base technology defined by the consortium is seen as limiting by AWS (our assertion, not AWS’); 2) Joining the consortium would validate a definition with which AWS isn’t aligned; and 3) AWS may feel it has a lead with its Annapurna acquisition and doesn’t want to validate its competitors.
Furthermore, our research leads us to speculate that AWS may be working deep within the U.S. government on a more advanced and comprehensive definition of confidential computing that it possibly intends to evolve as an official standard. It would be classic AWS to make a move like this as an aggressive and defensible strategy around confidential computing that is highly differentiated from its competition.
One of the premier members of the Confidential Computing Consortium is Google, along with many high-profile names, including Arm, Intel, Meta Platforms Inc., Red Hat, Microsoft Corp. and others.
In this Breaking Analysis, we’re pleased to welcome two experts on confidential computing from Google to unpack the topic: Nelly Porter, head of product for GCP Confidential Computing and Encryption, and Dr. Patricia Florissi, technical director in the Office of the CTO at Google Cloud.
What follows is a curated summary of our conversation with the full video embedded below. After each question we embed a video clip of the answers you can watch for added context.
Q: Nelly and then Patricia, please describe your respective roles at Google Cloud.
Porter: I work on a lot of interesting activities in Google with a focus on security and infrastructure security. And we’re talking about encryption and confidential computing is an important part of the portfolio. In addition, I collaborate with Google colleagues and our customers on secure software supply chains. Because you need to trust your software. Is it operating safely in your confidential environment? I work on having end-to-end confidence that your software and your environment are doing what you expect.
Florissi: I am a technical director in the office of the CTO, OCTO for short, in Google Cloud. And we are a global team. We include former CTOs like myself and senior technologists from large corporations, institutions and a lot of successful startups as well. And we have two main goals. First, we work side-by-side with some of our largest, most strategic customers and we help them solve complex engineering technical problems. And second, we focus with Google Cloud engineering and product management on emerging trends and technologies to guide the trajectory of our business. We are a unique group because we have created this collaborative culture with our customers. And within OCTO I spend a lot of time collaborating with customers and the industry at large on technologies that can address privacy, security and sovereignty of data in general.
Watch and listen to Nelly and Patricia describe their respective roles in their own words.
Q: Nelly, what is confidential computing from Google’s perspective – i.e. how do you define it?
Porter: Confidential computing is one of the tools in Google’s toolbox to help customers protect their data throughout its entire lifecycle. Confidential computing addresses the need to protect data and workloads. Not only when it is stored or in transit but also when it is being processed and used in the cloud. With confidential computing, Google can provide end-to-end protection of customer data and workloads, ensuring the data remains secure while still being able to extract insights and process it.
Watch Nelly Porter’s explanation of how Google defines confidential computing.
Q: Patricia, why do you think this confidential computing is such an important technology?
Florissi: Confidential computing is an important and transformative technology because it reduces the customer’s threat boundaries and attack surface. It is a natural progression from encrypting data in transit and at rest, to now encrypting data while in use. Confidential computing allows organizations to collaborate with each other while retaining the confidentiality of the data, which is beneficial for all industries, not just highly regulated ones. For example, in finance, bankers can collaborate to detect fraud while preserving the confidentiality and privacy of the data.
Q: Nelly, there is a narrative out there that says confidential computing is a marketing ploy by cloud providers placating people with cloud phobia. While you may strongly disagree, the argument is that confidential computing is just memory encryption and doesn’t address many other problems. Further, it’s overhyped by cloud providers. What would you say to this line of thinking?
Not surprisingly, Porter strongly disagrees with the premise that confidential computing is just marketing hype for memory encryption. According to Porter, the concept of confidential computing goes beyond just the mechanism of protecting customer data. Confidential computing offers stronger protection for tenants in multitenant cloud environments through cryptographic isolation, which provides customers with more trust in the security of their data. This cryptographic layer of isolation not only protects customers from other tenants in the environment, but also from mistakes made by the software provider or potential zero-day attacks. By providing this layer of protection, confidential computing eliminates some of the security concerns that customers may have when running their workloads in multitenant spaces or collaborating with sensitive data.
Q: Nelly, what’s architecturally different with confidential computing versus how operating systems and virtual machines have worked historically? Please explain and we’ll put up this slide for context.
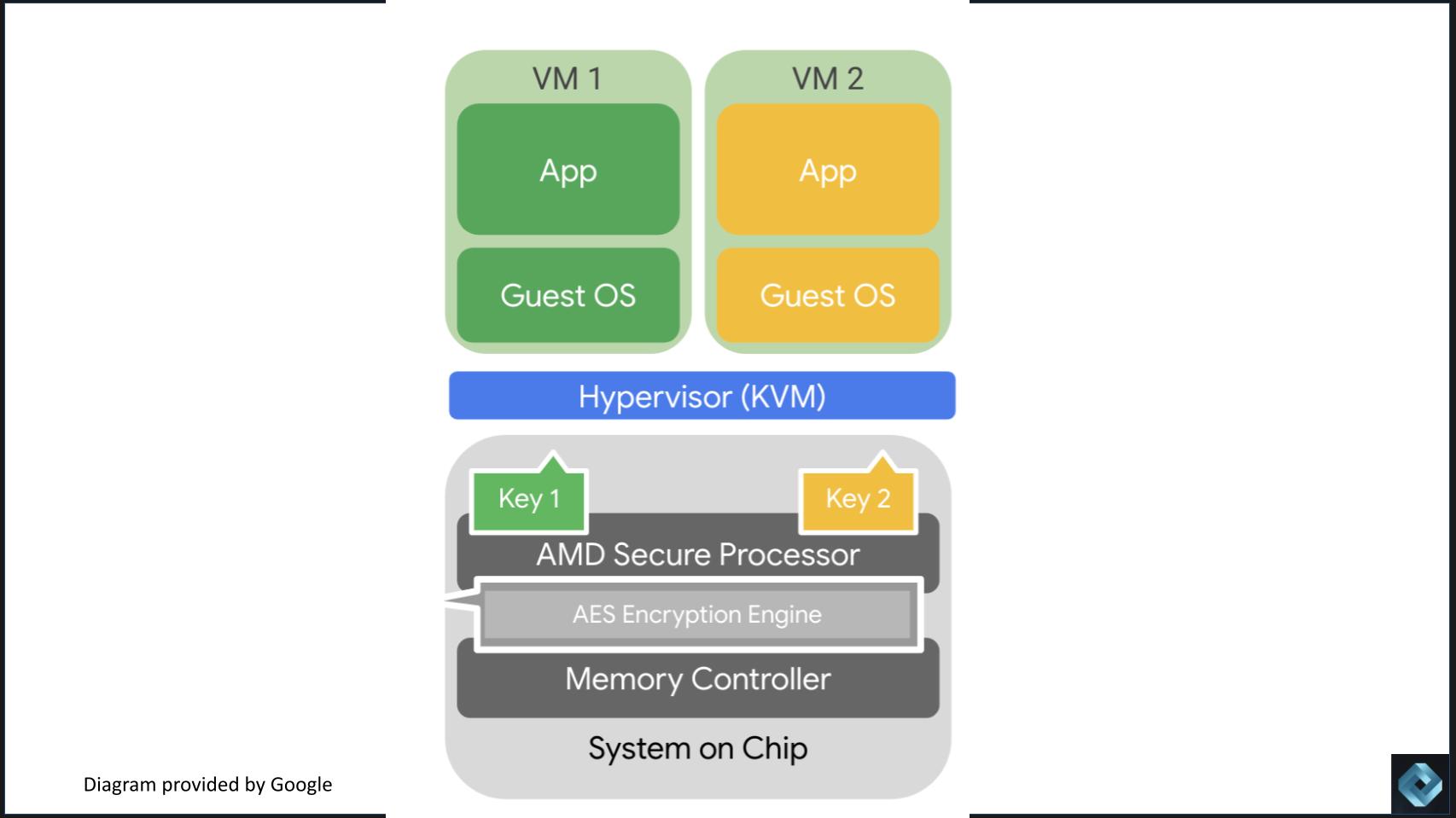
Porter: Google’s approach to confidential computing is designed to preserve three main properties: 1) Customers don’t need to change their code; 2) low latency; and 3) scalability. To achieve this, the entire system has to change to provide the security guarantees of confidential computing. The following are the key architectural changes in confidential computing:
Q: Patricia, what are the guarantees that these hardware-based technologies provide to cloud customers?
Florissi: Google makes the following promises to its customers with respect to confidential computing:
According to Google, these guarantees provide customers with the assurance that their systems are protected from unauthorized access and that their data has not been corrupted or impacted by outside actors.
Q: Nelly, how does Google ensure the compatibility of confidential computing with the existing systems and applications?
Porter: To ensure compatibility with existing applications when it comes to confidential computing, Google has done the following:
Q: Patricia, How will confidential computing ensure that data sovereignty and that privacy edicts are adhered to? Please explain Google’s approach and the key elements of this graphic.
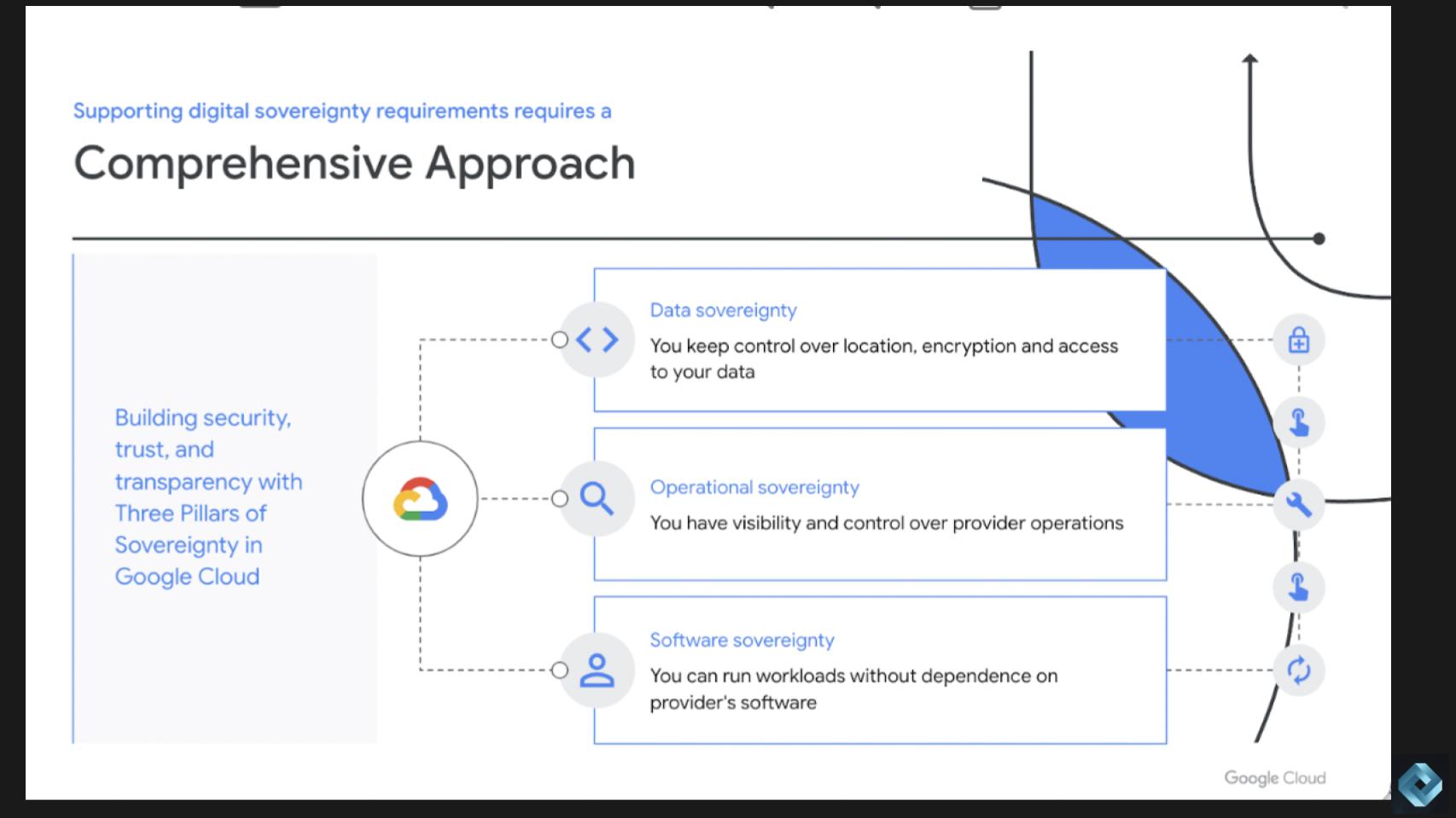
According to Florissi, data sovereignty is only one of the pillars to digital sovereignty. From Google’s perspective, digital sovereignty includes three pillars: 1) Data sovereignty; 2) operational sovereignty; and 3) software sovereignty.
Here’s a deeper-dive summary of the conversation:
According to Florissi, data sovereignty is typically concerned with two things: where the data resides (data residency) and ensuring the confidentiality, integrity and availability of the data (data protection). Confidential computing is at the heart of data protection.
However, there is another aspect of data sovereignty that is often overlooked, which is user control. This refers to what happens to the data when access is granted to it. Florissi underscores the importance of trusting that the processing of data will abide by the policies set by the user.
She also notes that there is a movement in regulation and initiatives, such as the International Data Space Association and GAIA-X, for providers and receivers of data to agree on a contract for how the data will be used. The challenge is to ensure that the data is used as intended once it crosses boundaries.
Google’s view is that confidential computing, combined with policy enforcement, is ensuring data sovereignty, particularly when it comes to user control. Policy enforcement guarantees that data is only processed within the confines of a confidential computing environment, that the workload is verified, and that the data will only be used in accordance with the confidentiality and integrity of the confidential computing environment.
Q: To both. What’s your prediction as to how widespread the adoption of confidential computing will be in 2023 and beyond?
Porter: My prediction in five, seven years as I stated, it’ll become like a utility. Ten years ago we couldn’t imagine that websites would have certificates and we would support encrypted traffic. Now we do, and it’s become ubiquitous. It’s exactly where our confidential computing is headed and heading. I don’t know if we are there yet yet. It’ll take a few years of maturity for us, but we’ll get there.
Florissi: I would double down on that and say in the future, in the very near future, you will not be able to afford not having it [confidential computing]. I believe as digital sovereignty becomes ever more top of mind with sovereign states and also for multinational organizations and for organizations that want to collaborate with each other, confidential computing will become the norm. It’ll become the default mode of operation. For the young technologists out there, it’s inconceivable to think that at some point in history data in transit was not encrypted. And I think that it will be inconceivable at some point in the near future to have unencrypted data while in use.
Watch and listen to Google’s technical experts predict the future of confidential computing.
Confidential computing is being touted by the cloud players as a promising technology for enhancing data privacy and security, but there are also those who remain skeptical of its merits and necessity. The truth probably lies somewhere in between, and it will depend on the specific implementation and the use case as to how effective confidential computing will be. Confidential computing is not a panacea for all security challenges, of course. But the beauty of the tech industry is because there’s so much competition confidential computing essentially comes at low or no cost to customers. And there is no obvious downside.
As with any new technology, it is important to carefully its adoption and make informed decisions based on the specific requirements and constraints of each individual situation. But the bottom line is: Silicon manufacturers are working with cloud providers and other systems companies to include confidential computing into their architectures. Competition will moderate price hikes and, at the end of the day, this under-the-covers technology essentially will come for free.
So we’ll gladly take it.
Many thanks to our guests today Google, Nelly Porter and Dr. Patricia Florissi. Alex Myerson and Ken Shifman are on production, podcasts and media workflows for Breaking Analysis. Special thanks to Kristen Martin and Cheryl Knight who help us keep our community informed and get the word out, and to Rob Hof, our editor in chief at SiliconANGLE.
Remember we publish each week on Wikibon and SiliconANGLE. These episodes are all available as podcasts wherever you listen.
Email david.vellante@siliconangle.com, DM @dvellante on Twitter and comment on our LinkedIn posts.
Also, check out this ETR Tutorial we created, which explains the spending methodology in more detail. Note: ETR is a separate company from Wikibon and SiliconANGLE. If you would like to cite or republish any of the company’s data, or inquire about its services, please contact ETR at legal@etr.ai.
Here’s the full video analysis:
All statements made regarding companies or securities are strictly beliefs, points of view and opinions held by SiliconANGLE Media, Enterprise Technology Research, other guests on theCUBE and guest writers. Such statements are not recommendations by these individuals to buy, sell or hold any security. The content presented does not constitute investment advice and should not be used as the basis for any investment decision. You and only you are responsible for your investment decisions.
Disclosure: Many of the companies cited in Breaking Analysis are sponsors of theCUBE and/or clients of Wikibon. None of these firms or other companies have any editorial control over or advanced viewing of what’s published in Breaking Analysis.
THANK YOU